Survey and taxonomy of information-centric vehicular networking security attacks
Information Centric Networks (ICNs) overcome the current IP-based networks weakness and aim to ensure efficient data distribution. The Main ICN features are location-independent naming, in-network caching, name-based routing, built-in security, and high mobility. ICN vehicular networks stratify the ICN architecture on the Vehicular Ad hoc Networks (VANETs) to reinforce a massive amount of data transmission and handle the critical time interests inside the vehicular networks while taking into consideration the vehicles’ high mobility. Original Equipment Manufacturers (OEMs) gather the real-time
Myocardial segmentation using contour-constrained optical flow tracking
Despite the important role of object tracking using the Optical Flow (OF) in computer graphics applications, it has a limited role in segmenting speckle-free medical images such as magnetic resonance images of the heart. In this work, we propose a novel solution of the OF equation that allows incorporating additional constraints of the shape of the segmented object. We formulate a cost function that include the OF constraint in addition to myocardial contour properties such as smoothness and elasticity. The method is totally different from the common naïve combination of OF estimation within
Myocardium segmentation in strain-encoded (SENC) magnetic resonance images using graph-cuts
Evaluation of cardiac functions using Strain Encoded (SENC) magnetic resonance (MR) imaging is a powerful tool for imaging the deformation of left and right ventricles. However, automated analysis of SENC images is hindered due to the low signal-to-noise ratio SENC images. In this work, the authors propose a method to segment the left and right ventricles myocardium simultaneously in SENC-MR short-axis images. In addition, myocardium seed points are automatically selected using skeletonisation algorithm and used as hard constraints for the graph-cut optimization algorithm. The method is based
In-silico development and assessment of a Kalman filter motor decoder for prosthetic hand control
Up to 50% of amputees abandon their prostheses, partly due to rapid degradation of the control systems, which require frequent recalibration. The goal of this study was to develop a Kalman filter-based approach to decoding motoneuron activity to identify movement kinematics and thereby provide stable, long-term, accurate, real-time decoding. The Kalman filter-based decoder was examined via biologically varied datasets generated from a high-fidelity computational model of the spinal motoneuron pool. The estimated movement kinematics controlled a simulated MuJoCo prosthetic hand. This clear-box
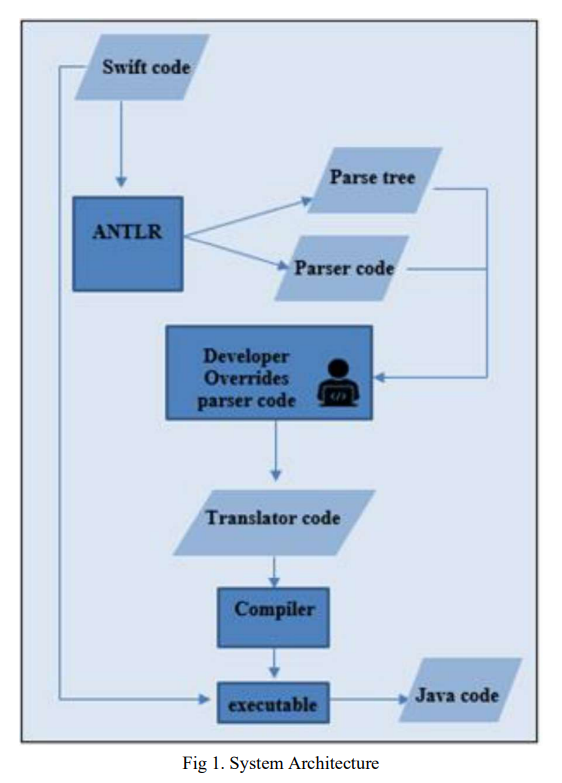
Trans-Compiler based Mobile Applications code converter: Swift to java
Numerous commercial tools like Xamarin, React Native and PhoneGap utilize the concept of cross-platform mobile applications development that builds applications once and runs it everywhere opposed to native mobile app development that writes in a specific programming language for every platform. These commercial tools are not very efficient for native developers as mobile applications must be written in specific language and they need the usage of specific frameworks. In this paper, a suggested approach in TCAIOSC tool to convert mobile applications from Android to iOS is used to develop the
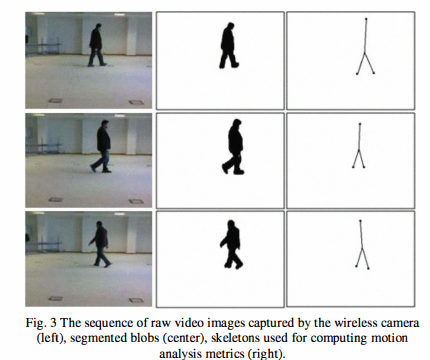
Ambient and wearable sensing for gait classification in pervasive healthcare environments
Pervasive healthcare environments provide an effective solution for monitoring the wellbeing of the elderly where the general trend of an increasingly ageing population has placed significant burdens on current healthcare systems. An important pervasive healthcare system functionality is patient motion analysis where gait information can be used to detect walking behavior abnormalities that may indicate the onset of adverse health problems, for quantifying post-operative recovery, and to observe the progression of neurodegenerative diseases. The development of accurate motion analysis models
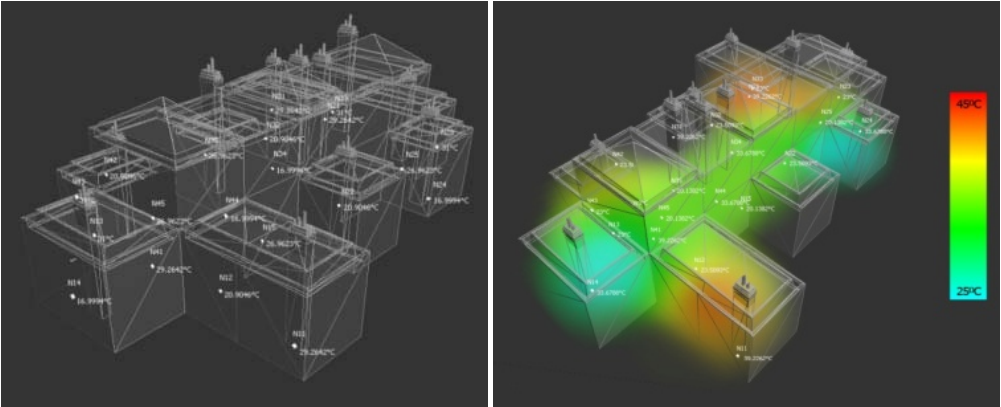
Monitoring and visualization of large WSN deployments
Recent developments in wireless sensor networks have ushered in novel ubiquitous computing applications based on distributed large-scale data acquisition and interactive interpretation. However, current WSNs suffer from lack of effective tools to support large network deployment and administration as well as unavailability of interactive visualization techniques required to explore and analyze captured sensing data, which is hindering the development of real-life WSN-based ubiquitous systems. Sensor Explorer addresses the above problems by providing modular efficient stream management engine
Cloud computing security: Challenges & future trends
Cloud computing is one of the most trendy terminologies. Cloud providers aim to satisfy clients' requirements for computing resources such as services, applications, networks, storage and servers. They offer the possibility of leasing these resources rather than buying them. Many popular companies, such as Amazon, Google and Microsoft, began to enhance their services and apply the technology of cloud computing to provide cloud environment for their customers. Although there are lots of advantages in using a cloud-based system, some issues must be handled before organisations and individuals
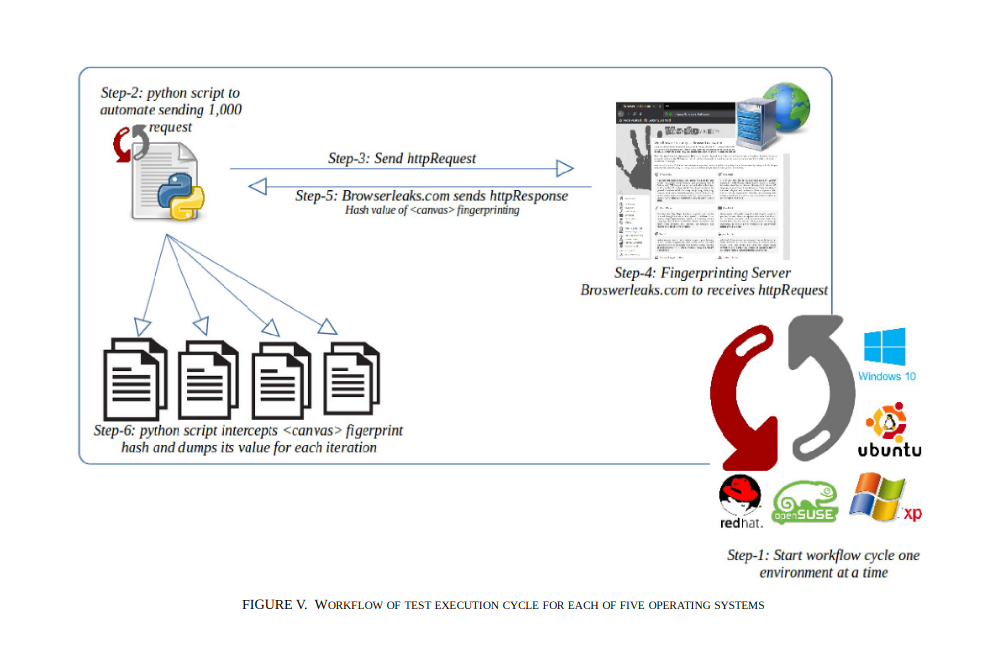
NONYM!ZER: Mitigation Framework for Browser Fingerprinting
Not only recent compelled cookies regulations have radically restrained their threats but also increased people awareness has played a fundamental part. This has placed huge pressure on enterprises to find alternatives to bridge this gap and satisfy business demands. Since then fingerprinting has gained enormous popularity. In this paper, we introduce 'nonym!zer' as a mitigation framework for browser fingerprinting. It helps to hinder or impede browser fingerprinting on desktop browsers that web servers use such as WebGL or Canvas technologies. © 2019 IEEE.
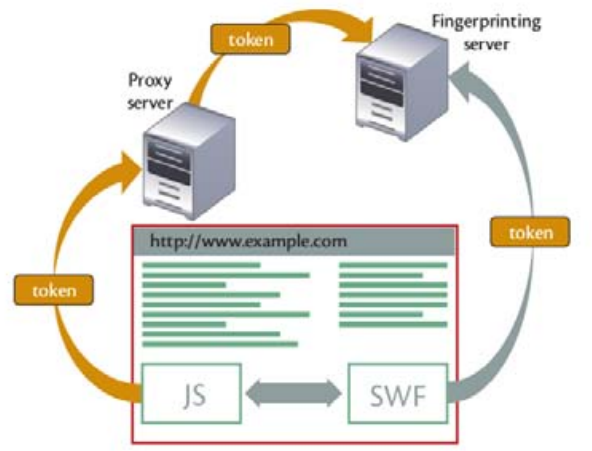
Browsers fingerprinting motives, methods, and countermeasures
With the continuous and aggressive competition in advertising businesses, uncontrollably desires have emerged to identify and classify consumers. It is proven that companies must have a clear definition of its target market. Based on this we have seen different ways to identify, analyze, and track consumers, either voluntarily or without their consent. Browser fingerprinting techniques have evolved from being privacy-friendly to privacy intrusive to serve these demands. This also has pushed privacy concerned people to save no effort to advance countermeasures. In this paper we introduce
Pagination
- Previous page ‹‹
- Page 14
- Next page ››
